Research on secure NTP method based on message digest encryption
-
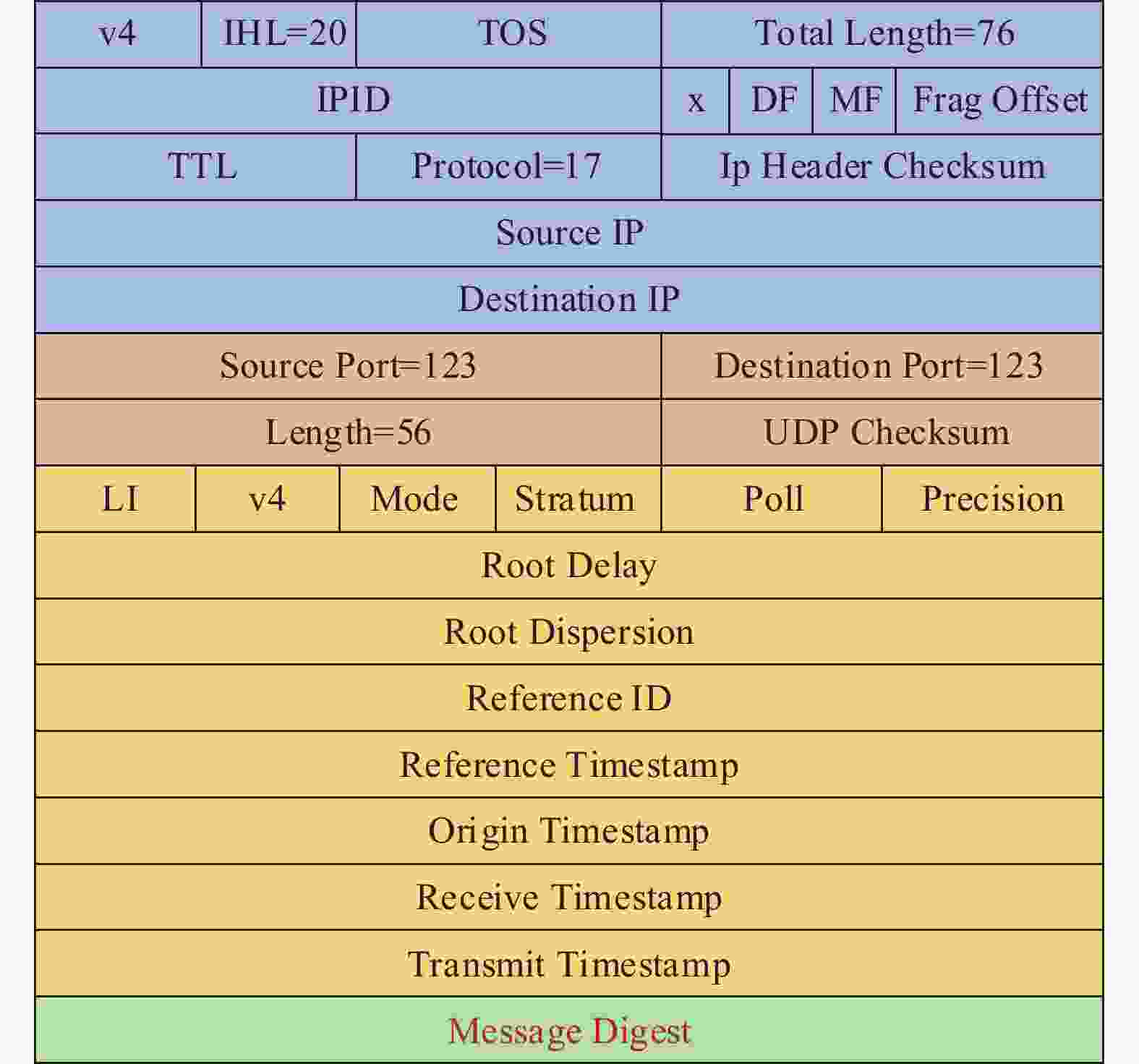
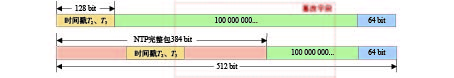
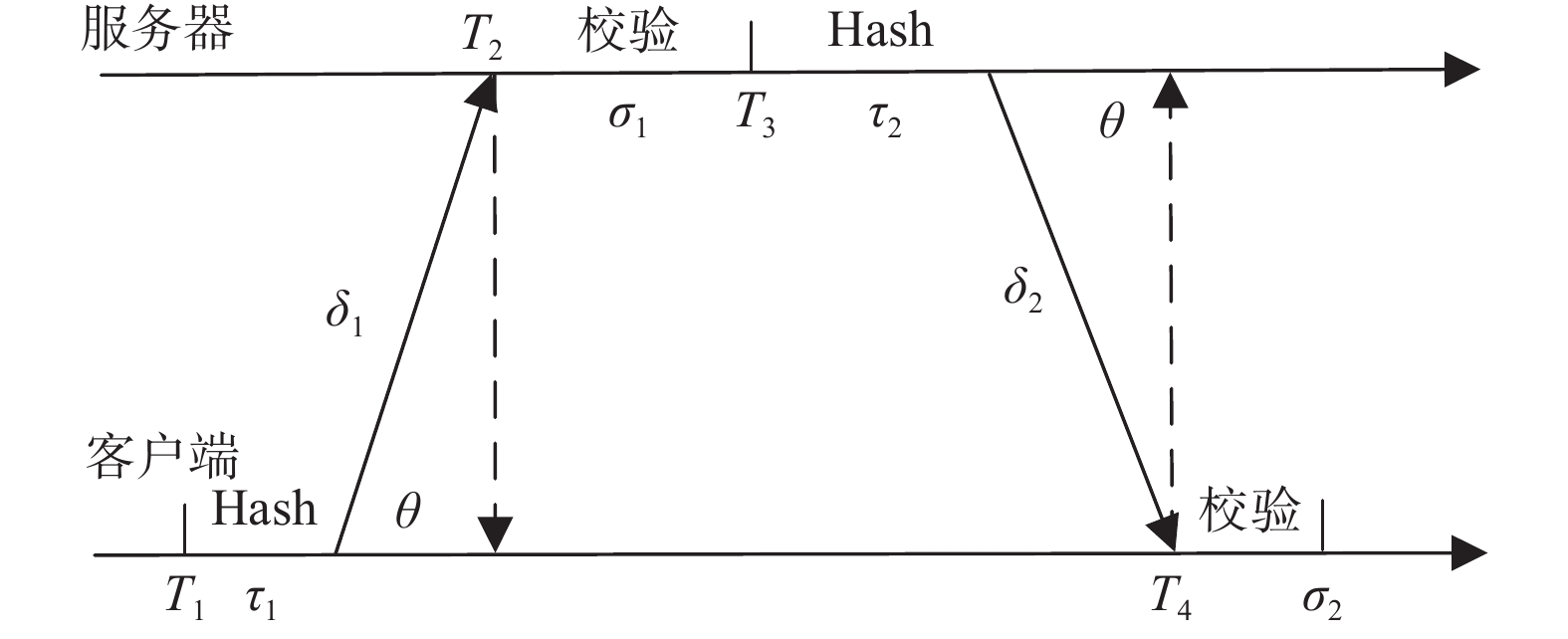
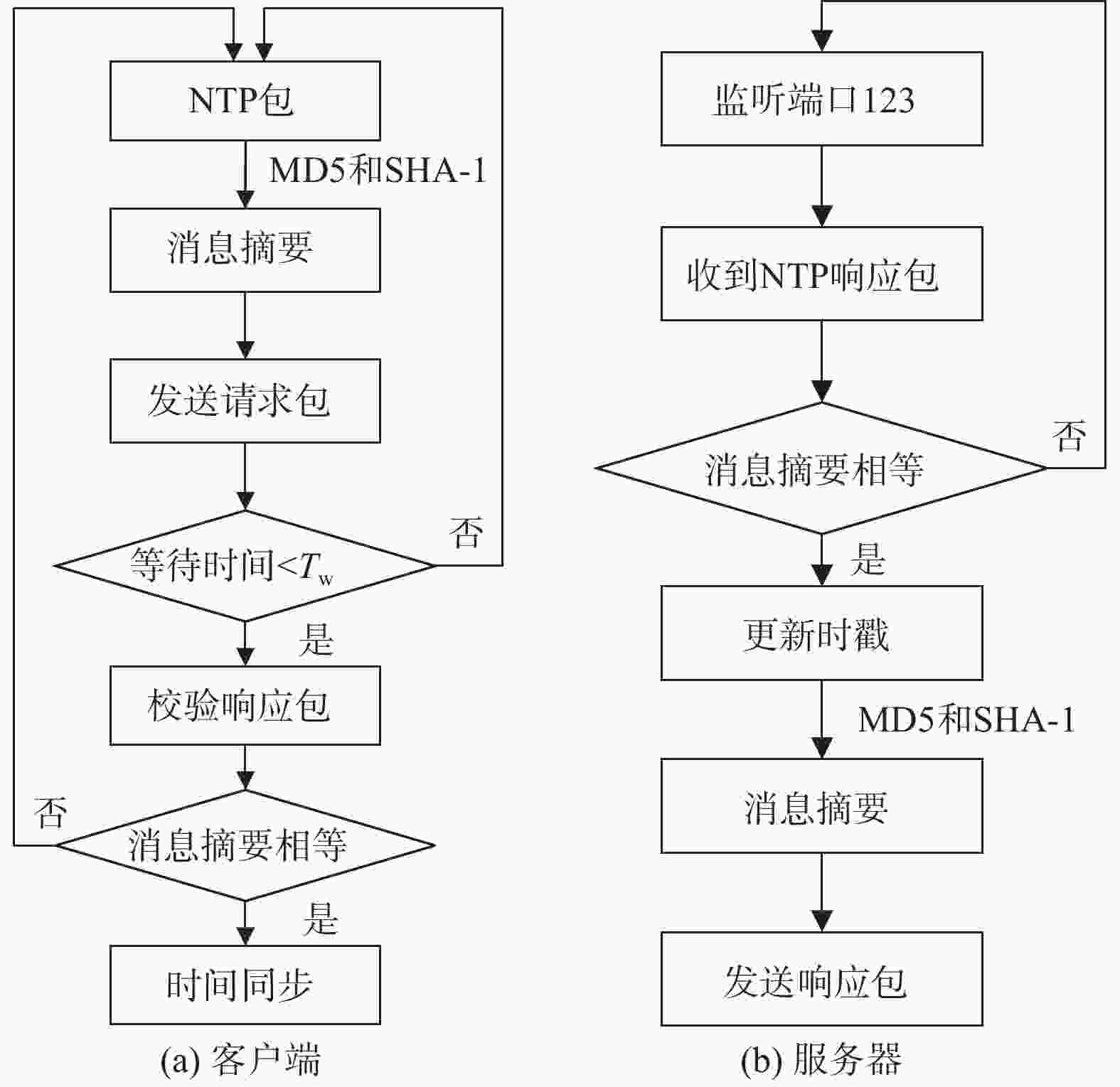
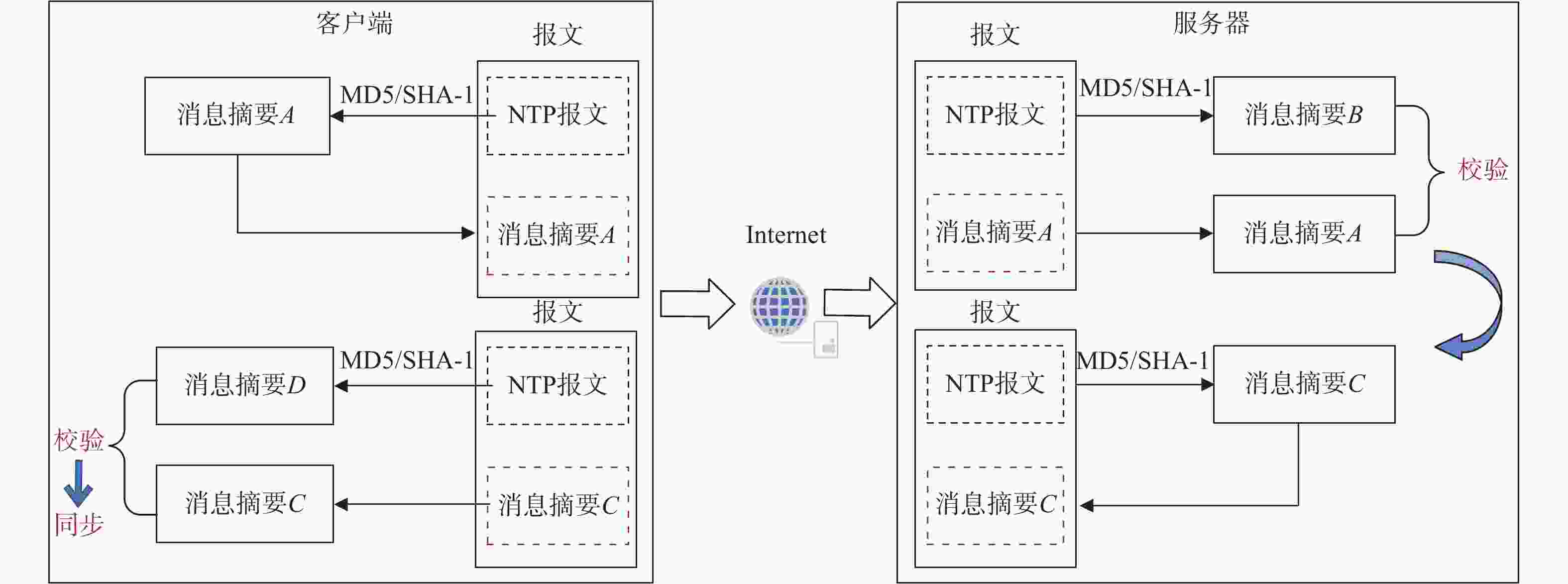
摘要: 目前,以网络时间协议(NTP)为主要的时间协议应用于有线网络中的时间同步,其在广域网中可以实现十几毫秒、局域网中实现几毫秒的同步精度. 然而,由于协议的开放性,其在无安全防护的情况下极易受到网络攻击,这给需要高安全的客户带来潜在的风险. NTP可以增加安全策略来应对可能的安全风险,将消息摘要(MD)中的MD5和安全散列算法(SHA)中的SHA-1引入NTP算法,有效地验证了数据完整性,防止数据包被篡改,以保证时间同步的安全性. 进一步,针对这两类算法提出对NTP包关键数据帧Hash加密,在保持良好同步精度的同时可进一步提高时间同步的安全性. 通过实验对比了MD5和SHA-1算法加入所带来同步效果的影响. 结果表明:在MD5和SHA-1算法加入后,NTP依然能保持毫秒级的同步性能,这对于实现NTP安全时间同步方法具有重要意义.Abstract: At present, the network time protocol (NTP) is the main time protocol used for time synchronization in wired networks. It can achieve a synchronization accuracy of more than ten milliseconds in wide area networks and a few milliseconds in local area networks. However, due to the openness of the protocol, there is no security protection. Under the circumstances, it is extremely vulnerable to network attacks, which brings potential risks to customers who need high security. The NTP protocol can increase security strategies to deal with possible security risks. The message digest algorithm 5 (MD5) and the secure hash algorithm (SHA-1) message digest algorithm is introduced into the NTP protocol algorithm, which is effective to verify data integrity and prevent data packets from being tampered with to ensure the security of time synchronization. Further, for these two types of algorithms, Hash encryption of key data frames of NTP packets is proposed, which can further improve the security of time synchronization while maintaining good synchronization accuracy. Experiments have compared the influence of the synchronization effect brought by the addition of the algorithm. The results show that after the message digest algorithm is added, NTP can still maintain millisecond-level synchronization performance, which is of great significance to the realization of the NTP secure time synchronization method.
-
Key words:
- message digest (MD) /
- timestamp /
- the network time protocol (NTP) /
- offset /
- delay /
- anti-tampering
-
表 1 MD5算法和SHA-1算法对比
特征 MD5算法 SHA-1算法 消息摘要长度/bit 128 160 产生相同消息摘要所需操作/次 264 280 轮数/次 4 4 迭代次数 64 80 表 2 不同算法统计数据对比
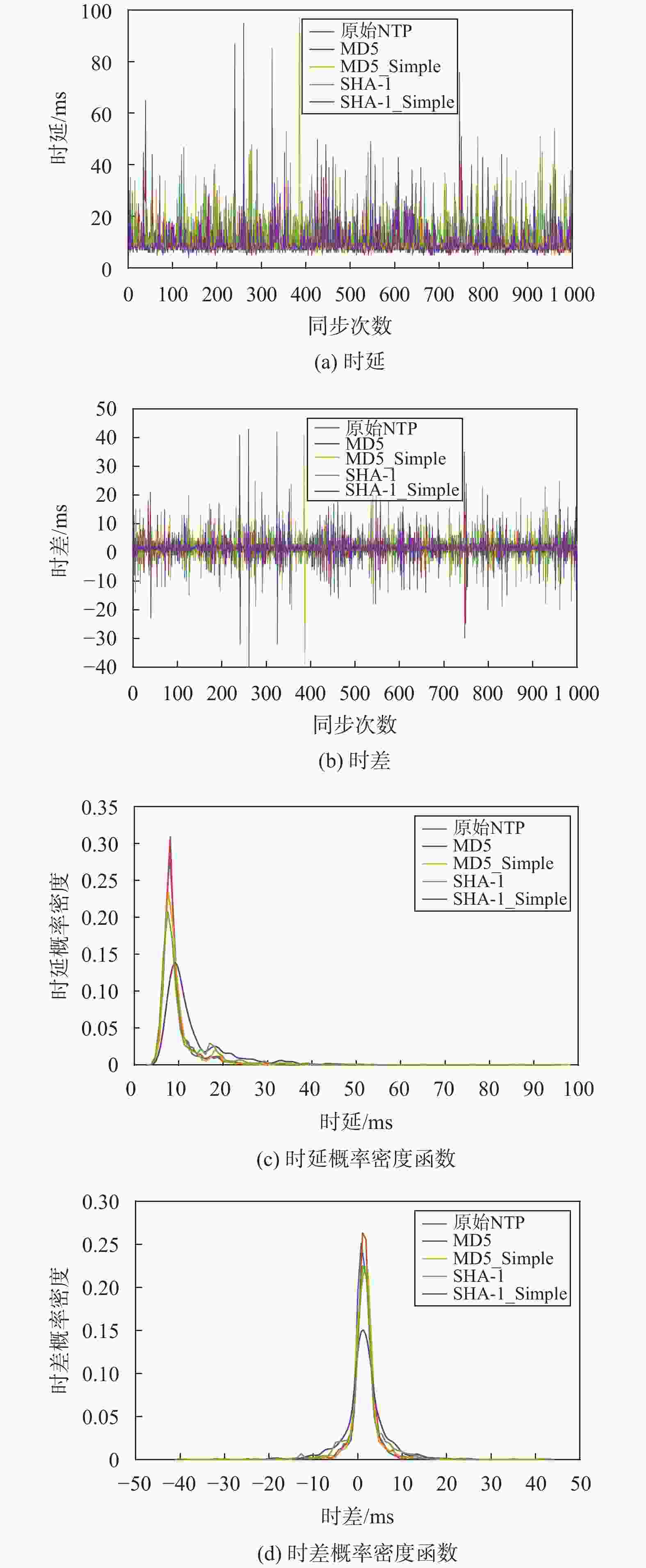
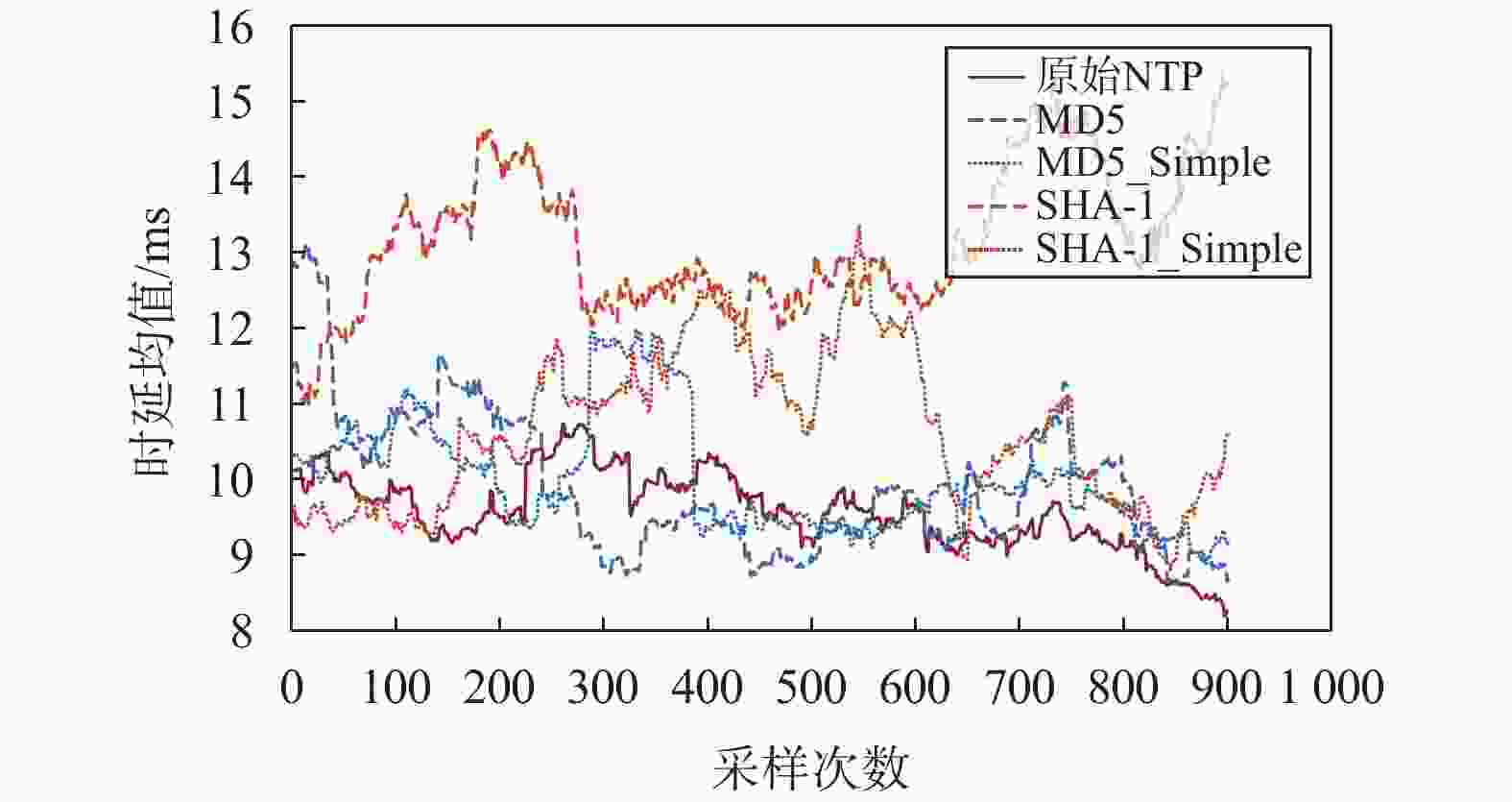
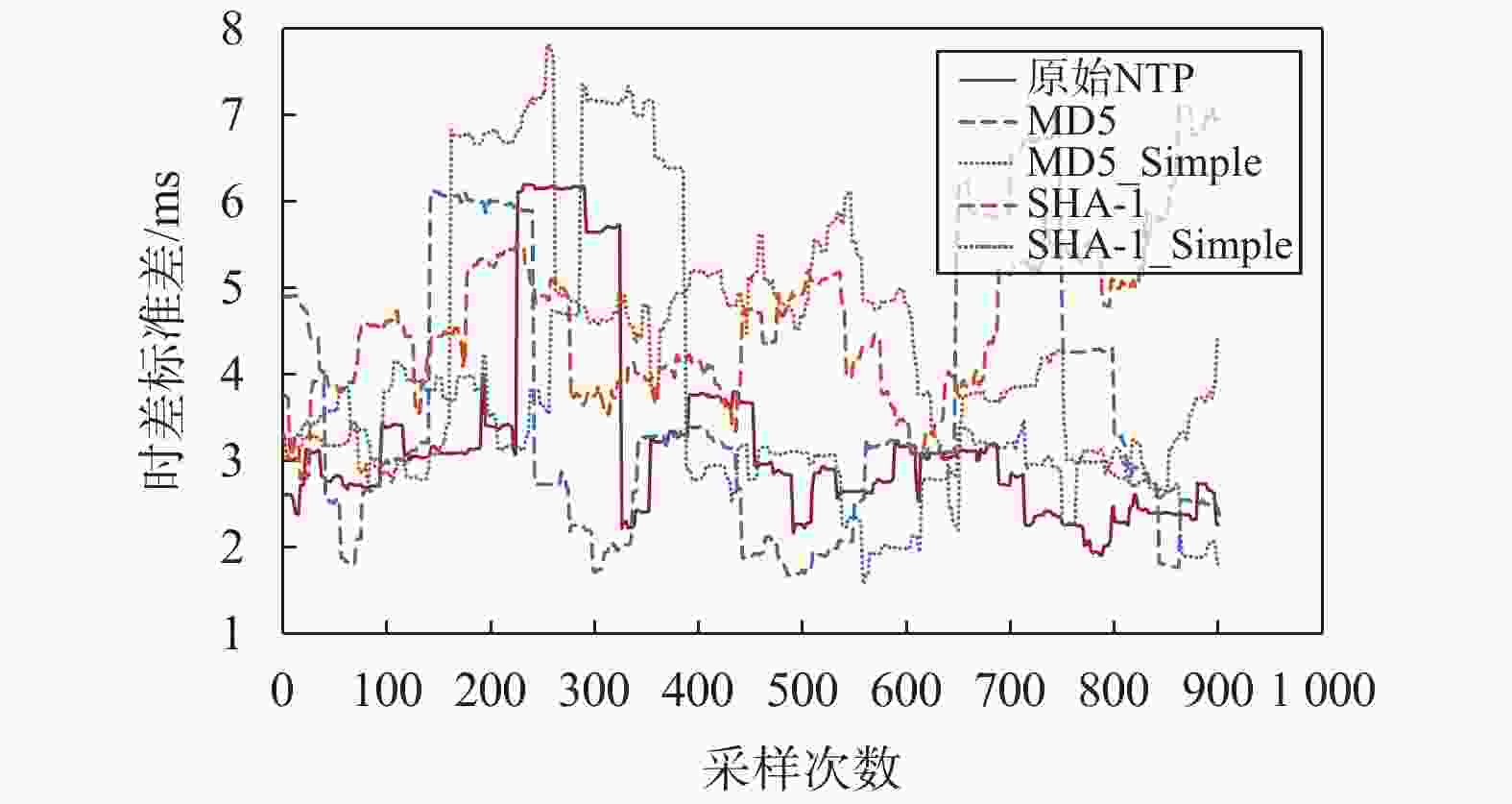
ms 算法 时延均值 时差标准差 原始NTP 9.538 0 3.295 1 MD5 10.004 0 3.926 2 MD5_Simple 9.985 0 3.639 7 SHA-1 13.192 0 4.789 0 SHA-1_Simple 10.631 0 4.462 7 表 3 不同算法耗时对比
ms 算法 波动范围 均值 原始NTP 0.3~15 4.976 3 MD5 0.4~17 5.198 0 MD5_Simple 0.4~16 4.973 9 SHA-1 0.4~16 5.224 5 SHA-1_Simple 0.4~16 5.361 9 表 4 本地流量增加后不同算法统计数据对比
ms 算法 时延均值 时差标准差 原始NTP 14.284 0 6.121 8 MD5 17.605 0 7.054 8 MD5_Simple 16.415 0 7.075 7 SHA-1 20.332 0 7.967 9 SHA-1_Simple 18.275 0 8.006 3 -
[1] LÉVESQUE M, TIPPER D. A survey of clock synchronization over packet-switched networks[J]. Communications surveys and tutorials, 2016, 18(4): 2926-2947. DOI: 10.1109/COMST.2016.2590438 [2] 李培基, 李卫, 朱祥维, 等. 网络时间同步协议综述[J]. 计算机工程与应用, 2019, 55(3): 30-38. DOI: 10.3778/j.issn.1002-8331.1809-0008 [3] BISHOP M. A security analysis of the NTP protocol version 2[C]//The 6th Annual Computer Security Applications Conference, IEEE, 1990. DOI: 10.1109/CSAC.1990.143746 [4] 黄九梅, 洪锡联, 赵英. 网络时间同步及其安全性研究[J]. 中国科技信息, 2008(16): 97-98. DOI: 10.3969/j.issn.1001-8972.2008.16.050 [5] 刁造翔, 章小宁, 王淑君, 等. 局域网条件下的NTP伪造服务器攻击技术[J]. 电子信息对抗技术, 2016, 31(6): 63-68. DOI: 10.3969/j.issn.1674-2230.2016.06.013 [6] 彭栋, 郭伟. 安全网络授时服务技术研究[J]. 时间频率学报, 2018, 41(1): 37-45. [7] LANGER M, TEICHEL, K, SIBOLD D, et al. Time synchronization performance using the network time security protocol[C]//European Frequency and Time Forum (EFTF), 2018. DOI: 10.1109/EFTF.2018.8409017 [8] KOGCE M, SISECI N E. A new approach to security of N TP via SSL certificates[C]// The 1st International Informatics and Software Engineering Conference (UBMYK), 2019. DOI: 10.1109/UBMYK48245.2019.8965454 [9] 周琴琴. 基于Hash函数的MD5和SHA-1加密算法研究及其硬件实现[D]. 合肥: 安徽大学, 2012. [10] 王小云, 于红波. 密码杂凑算法综述[J]. 信息安全研究, 2015, 1(1): 19-30. [11] 王孟钊. SHA1算法的研究及应用[J]. 信息技术, 2018(8): 152-153, 158. [12] 吴松魁. 基于UVM的HASH类算法IP核验证[D]. 西安: 西安电子科技大学, 2020. -
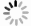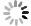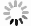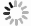



 下载:
下载: